In this Exception Handling in UFT and Synchronization article, we are going to learn the below topics –
· Exception Handling in UFT
· Recovery Scenario in UFT
· Synchronization in UFT
UFT Tutorial – Table of Content
- UFT Tutorial #1: UFT Overview
- UFT Tutorial #2: UFT Setup – Download, Install, License Configuration and ALM Connection
- UFT Tutorial #3: UFT Object Repository
- UFT Tutorial #4: UFT Actions & Function Library
- UFT Tutorial #5: UFT Parameterization
- UFT Tutorial #6: VB Scripting in UFT
- UFT Tutorial #7: Step by Step Guide to Create Test Case in UFT
- UFT Tutorial #8: Exception Handling in UFT
- UFT Tutorial #9: Recording in UFT with Checkpoints & Dictionary Object
- UFT Tutorial #10: UFT Interview Questions and Answers
Exception Handling And Synchronization in UFT
Exceptions in UFT:
An exception is nothing but an undefined event or error. In automation testing, if any errors or events are encountered which are not handled through the automated steps, they are treated as exceptions. Exceptions can be occurred due to any of the below scenarios –
Bug –
Any new bugs or issues in the application which are not handled properly can be the reason for an exception.
Environment Error –
Environment outage or network latency can create exceptions as the expected screens/pages are not available.
Test data –
Due to the correctness or invalid test data, an exception can occur during the test execution.
Technical issue –
If the test case is not designed properly, an exception can occur during the test run.
Undefined popup –
Any undefined popups such as Security, timeout, Information, Warning also can be the sources of exception.
The impacts of exceptions are –
- Test execution failure.
- Need more effort to perform debugging/ re-execution.
- Increase the cost and maintenance efforts.
- Automation goal, i.e., ROI, can not be achieved.
Exception Handling in UFT:
It is not possible to handle all the unexpected errors through automation. But if we use exception handling during the scripting, the chances of unexpected error can be minimized. The tool provides some mechanism for exception handling in UFT. The approaches for exception handling in UFT are –
- Recovery Scenario in UFT
- Scripting and Test Setting
- On-Error-Resume-Next statements for VBS
- Using Test Settings
- Using Exit Statement
Recovery Scenario in UFT:
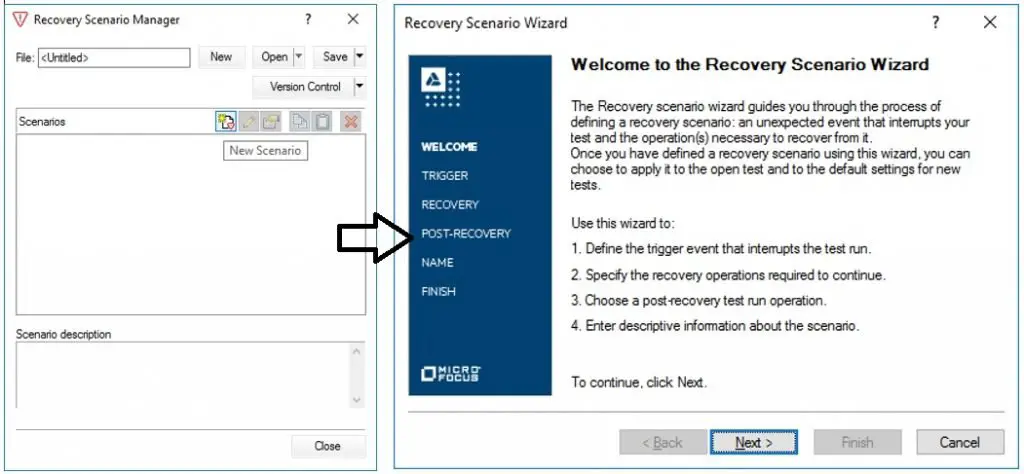
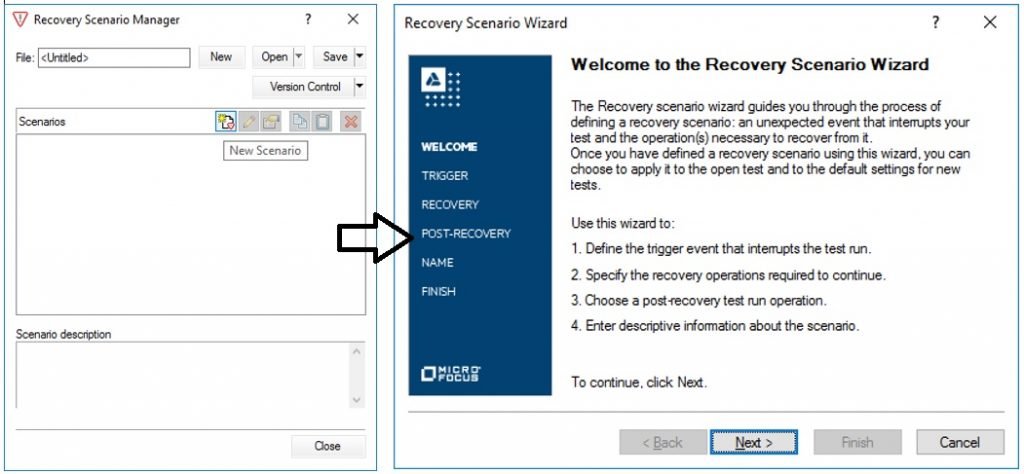
A recovery scenario in UFT is an approach to handle unexpected events/ errors during the execution. The “Recovery Scenario Manager” wizard helps to manage the recovery scenarios. We can open the “Recovery Scenario Manager” by using the navigation “Resources → Recovery Scenario Manager.” While creating the recovery scenario, we need to perform three configuration steps in UFT based on the requirements. Those are Triggering Event, Recovery operations, and Post-Recovery Test Run Options.
Triggering Event:
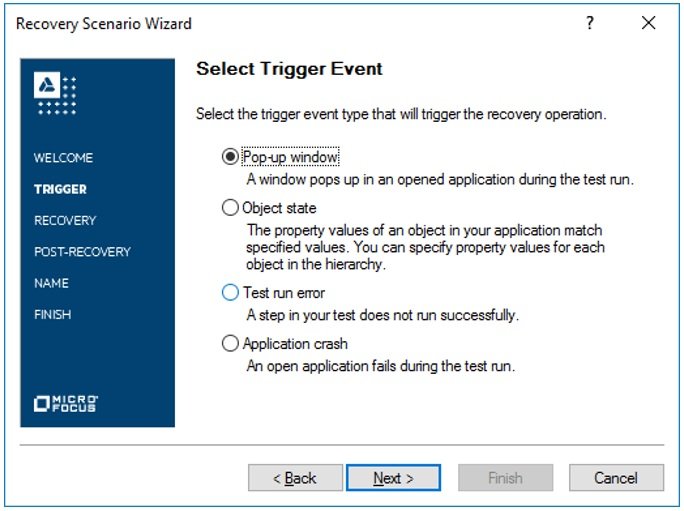
It defines the unexpected events, which will call the Recovery Scenario. The different options/ events available during the creation of recovery scenario in UFT are specified below –
- Unexpected pop-up windows.
- Errors which may appear due to Object State.
- Errors during the Run time.
- Application Crash.
The main usage of recovery scenario to handle different types of unexpected errors and perform some predefined steps against each types of error.
Recovery operations:
Based on this configuration, UFT will perform a set of actions for recovery purposes.
Post-Recovery Test Run Options:
After the recovery, we need to configure these options to execute some predefined steps which may be required.
Step by Step guide to create a Recovery Scenario in UFT:
Now, we will learn how to create the recovery scenario in UFT based on an example.
Example – An error popup (missing mandatory fields) is appearing while trying to save the records intermittently. In this particular situation, we need to click on the OK button to close the error popup and re-execute the current step as a post-recovery action.
- Step1# We need to open the “Recovery Scenario Manager” from the navigation menu “Resources → Recovery Scenario Manager.”
- Step2# Click on the “New Scenario” icon to open the wizard to create a recovery scenario in UFT and click on the Next button to select the triggering event.
- Step3# We need to select the “popup window” radio option as the Trigger Event of the recovery scenario and click on the Next button.
- Step4# Now, we need to click on the pointing hand icon and identify the error popup window using the mouse. UFT tries to identify the popup based on the window title and text. So, after the identification, we can use a regular expression to make it robust.
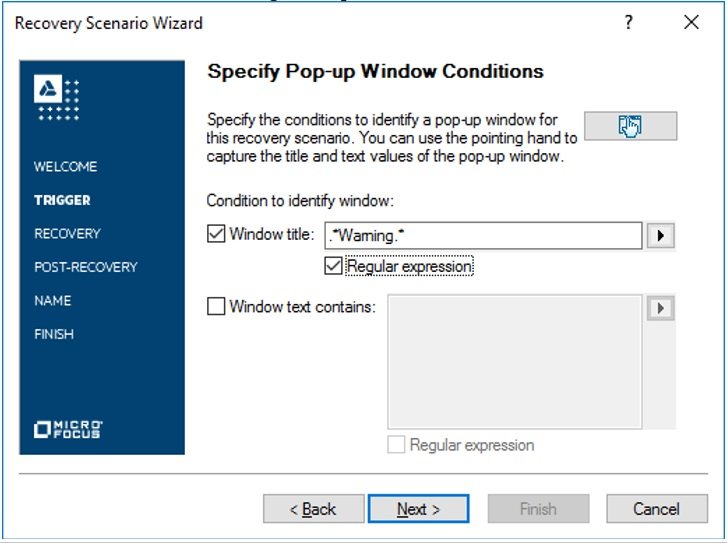
- Step5# Initially, recovery operations are not set. To define the recovery operation, we need to click Next.
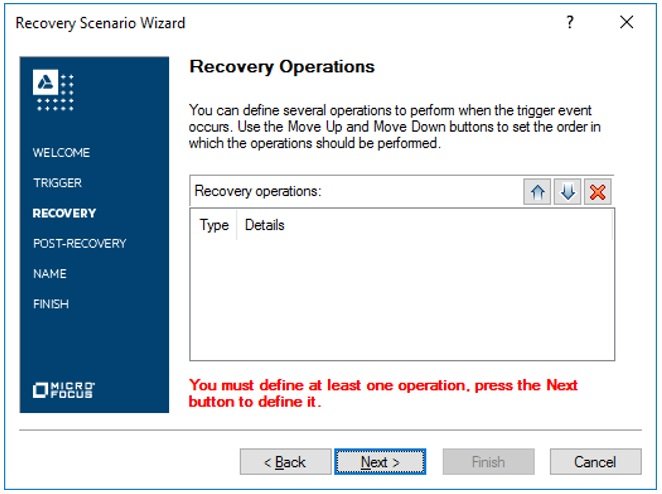
- Step6# Now, based on our requirement, selecting “Keyboard or mouse operation.” On the next screen, select the “Click button with label” option using the pointer hand option and click on the Next button.
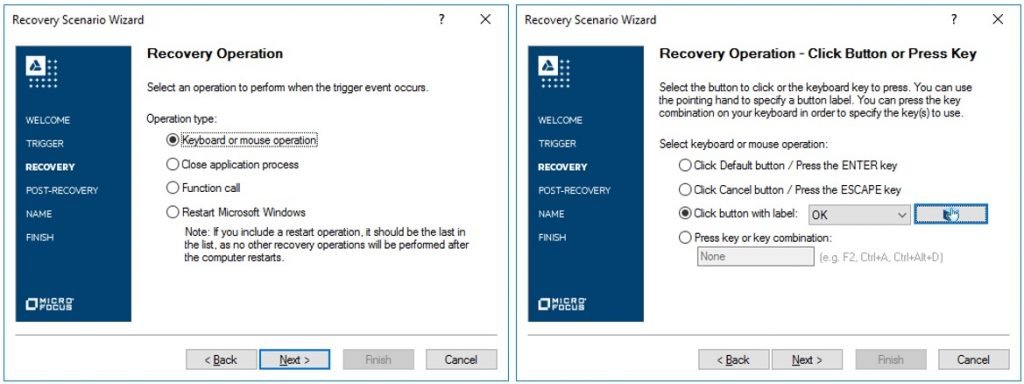
- Step7# Recovery operation is defined now. Here, after unchecking the option “Add another recovery operation”, we need to click on “Next” button to proceed.
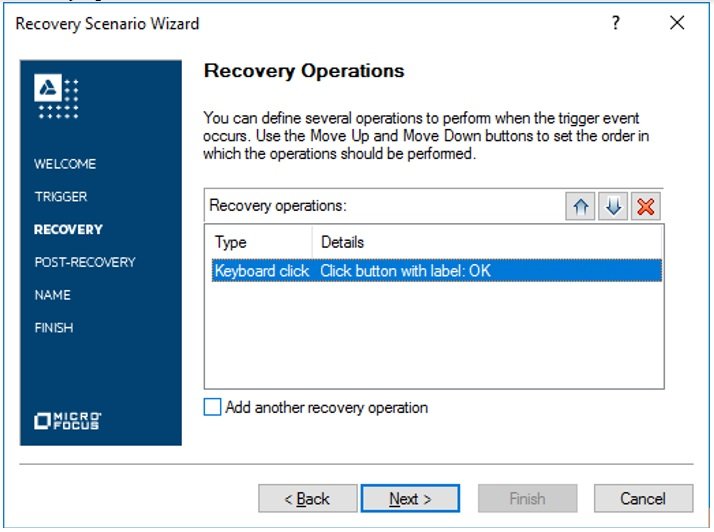
- Step8# We will select the option “Restart current test run” in the Post-Recovery section and provide the scenario name on the next screen. After entering the name, we need to click on “Next” button to proceed to the final screen.
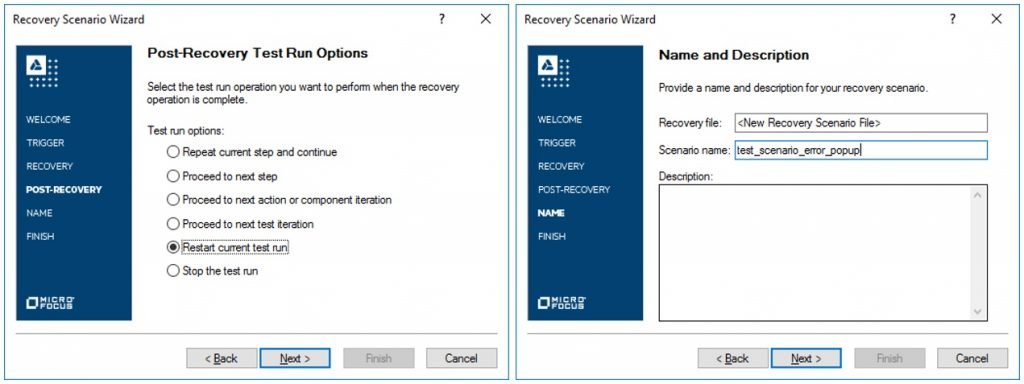
- Step9# Based on the requirement, we can add this scenario to the current test or to the default test settings. Now, to close the “Recovery Scenario” wizard in UFT, we need to click on the “Finish” button.
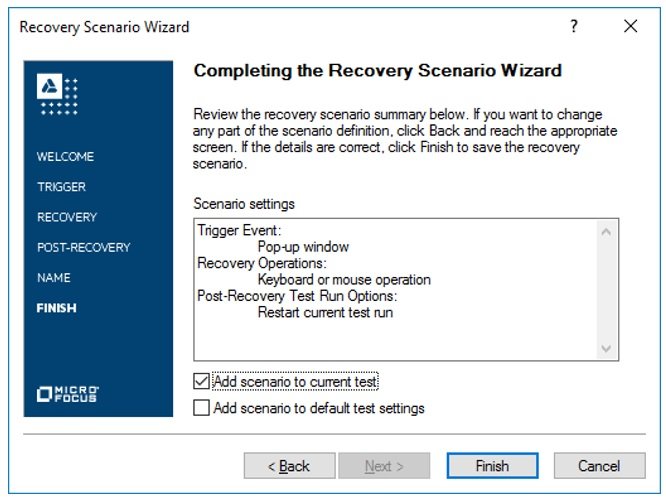
- Step10# Now, we need to save the recovery scenario in an external file and close.
Scripting and Test Setting Approach:
On-Error-Resume-Next statements:
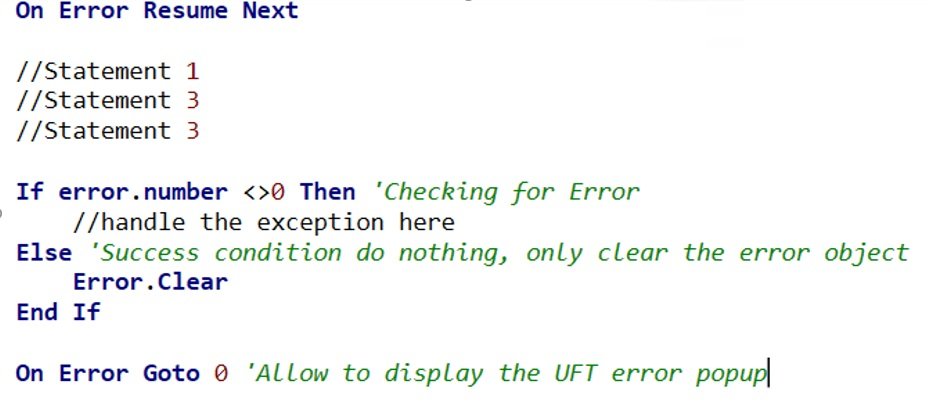
It was using the On-Error- Resume-Next statements; the exception can be handled partially. In this approach, the test script block should be started with “On Error Resume Next” statements. It defines that in case of any error, execution will will skip the present step and continue with next step. After that, by checking the error, we can handle the exceptions. Important keywords are –
On Error Resume Next –
In case of error, UFT will not raise an error message; instead of that, execution will move to the next step.
On Error Goto 0 –
It will work in reverse procedure with comparison to the above keyword i.e., in case of any unhandled error, an UFT error popup will be thrown with three options – retry, skip and stop.
Error.Description –
It stores the error description.
Error.Number –
It holds the error number. For success, the value is zero.
Error.Clear –
It reset the Error object.
Using Exit Statements:
UFT provides some predefined methods which will allow us to handle the exceptions through the scripts. The frequently used methods are –
ExitActionIteration –
Use to exit the current iteration of the action. ExitAction – Exits the current action.
ExitTest –
UFT will exit from the test execution.
ExitTestIteration –
Skip the current test iteration and the execution will be continued with the next test iteration.
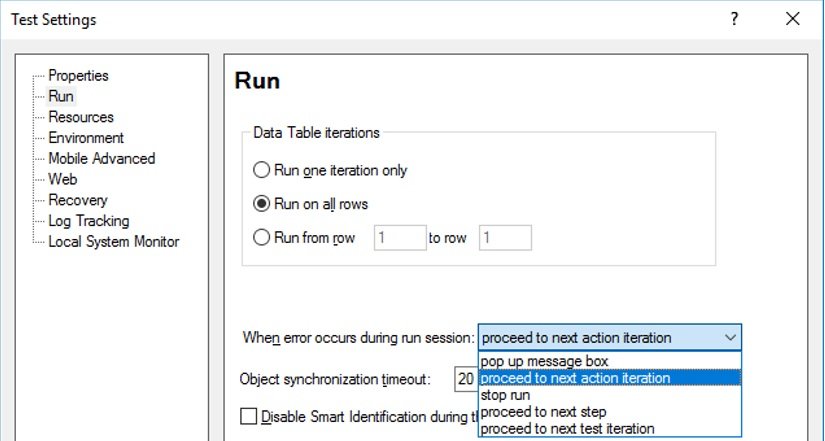
Using Test Settings:
We can configure the recovery steps by selecting any of the below options from the UFT Test Setting wizards (Run Tab).
Pop up message box –
In case of any error, UFT shows a popup message with error details.
Proceed to next action iteration –
UFT will execute the next action iteration when an exception has occurred.
Stop run –
Execution will be stopped.
Proceed to next step –
Execution will be resumed from the next step.
Proceed to next test iteration –
UFT will execute the next test iteration for any error.
Synchronization in UFT:
Synchronization in UFT is an approach to define the time interface between the tool and the application under test. If the application behavior is slower than the expectation of UFT, the test will be failed. So, synchronization in UFT is another important topic for test automation.
Chances of synchronization errors can be minimized by using either of the below approaches –
Wait:
The default Wait(timeout) statement is a static method to handle the synchronization errors. Here, timeout denotes the hardcoded wait time in seconds. During the execution, the script will wait for specific time at this point. We need to define the value of timeout based on the application responses.
WaitProperty in UFT:
To use the method WaitProperty in UFT, we need to specify the property name, the expected value of the property and the maximum wait time in mili-seconds. This is a dynamic way to handle the synchronization. Here, the execution will wait till the the property value satisfies with the expected value in the application. If the property value does not match, after the spefied maximum timeout, the script will proceed with the next step. Example –
Window(“<windiow name>”).WinListView(“<view name>”).WaitProperty “visible”,true,20000
- Loop:
This is an indirect way to handle the synchronization dynamically. We can use a loop with a condition to check the the object’s property value does not satisfied with expected value. In the loop statement, we can provide a small time out value using the Wait(timeout) statement. So, the checking will be done after each timeout and loop will be continued until the object is visible.
- Test Setting:
We can define the synchronization timeout in the Test Setting wizard (Run tab and web tab for web navigation timeout). Based on this configuration, UFT will wait for the test objects.
Conclusion:
In this “Exception Handling in UFT ..” article, we have learned about exception handling in UFT along with recovery scenarios and synchronization in UFT. Please click here to get more information on “Exception Handling” from the Microfocus support portal.